Your computer has a secret to tell you. Hidden away in its file system is a file called hosts. This file is the most efficient way to block websites. The hosts file can be used to block ads, to block pornography, to block gambling sites and to block accidental access to malicious web servers. Any website that you want to block can be blocked using the hosts file.
The hosts file matches domain names to web server IP addresses. The file is read by a computer when a website is requested. Requests to view pages of a website listed in the hosts file are directed to the IP address listed alongside the website’s domain name by the computer.
This method of site blocking works with Windows, Linux, Unix, Posix, Android, Symbian, Mac OSx, iOS and nearly all other operating systems. The OS can be installed on a desktop, laptop, netbook, tablet or smartphone or web server.
The hosts file can be used to
- prevent access to websites
- block ads displayed by ad servers
- stop malware being delivered by malicious websites
- redirect requests to preferred alternatives
Effective use of the hosts file can make web pages load faster and can make browsing the web safer.
How to Edit the Linux Hosts File
- Open the hosts file for editing by typing the following command into a terminal
gksu gedit /etc/hosts
or, if you use KDE
kdesudo kate /etc/hosts
- Move on to Step Two: The Hosts File Format
How to Edit the Windows Hosts File
- Stop the DNS Client service by clicking Start and typing services.msc into the Run dialogue then in the window that opens, double-click the DNS Client service and set the startup type to manual and disable the service before closing the window.
- Locate the Hosts file at c:\windows\system32\drivers\etc\hosts.
- Right-click “hosts”, select Properties then untick Read Only before clicking OK.
- Navigate to Start > All Programs then right-click Notepad and select Run as Administrator.
- In Notepad, click File > Open then browse to C:\windows\system32\drivers\etc\hosts.
- Move on to Step 2
Re-lock your Hosts file as Read Only once you have saved your edits.
Antivirus programs might lock the Windows hosts file to prevent edits to it. Check your antivirus settings if you can’t save your edits.
Step Two: The Hosts File Format
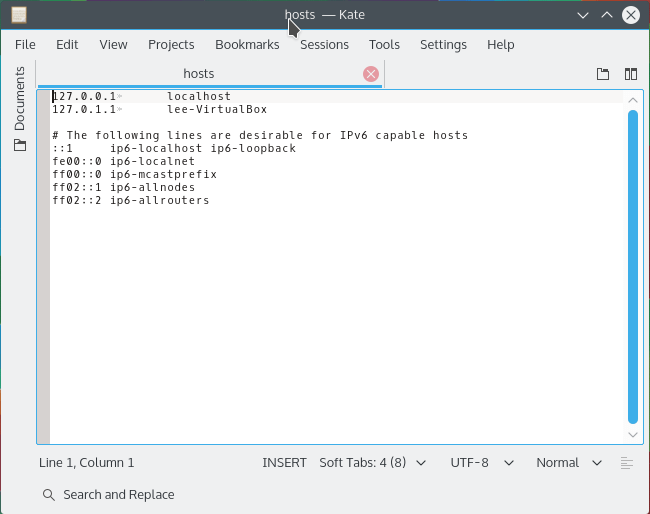
A hosts file stores rows of IP address and domain name pairings. Each IP address is separated from its associated domain by either a space, several spaces or a tab.
Each row of the file that contains an IP address to domain name mapping tells the computer the IP address of the web server that hosts files for the domain name.
A hosts file might have a hash symbol (#) in front of some rows. The hash symbol is used to tell a computer to ignore the row. This effectively deactivates the rule.
Domain names in the hosts file do not include their protocol prefix e.g. http:// or https. Only the root domain name is used.
127.0.0.1 localhost 127.0.0.1 example.com # 127.0.0.1 test.com
To block access to a website, create a list of websites you wish to block and associate each domain name with the IP address 127.0.0.1. The IP address is always placed on the left. The domain name (AKA ‘host name’) is always placed on the right.
Step Three: Get a List of Bad Hosts
There are plenty of ready compiled and regularly updated lists of bad hosts. These are called host lists. Host lists are easy to install and are normally provided free of charge.
The following host lists are the ones we at JournalXtra recommended.
- Hosts-File (Liberal)
- MVPS (Liberal to Moderate)
- RLWPX (Moderate to Strict)
- HostsFile (Strict)
No list has blocks for all malicious websites, all ad servers, all gaming or all sites undesired by the most conservative among us.
The list of bad hosts provided by HostsFile is the most restrictive. This list is perfect for the conservative minded members of society. I think HostsFile is compiled to meet the restricted Internet browsing needs of conservative Muslim internet users.
The website block lists provided by Hosts-File and MVPS are suited to those who hold liberal to moderate views about what should and should not be looked at. These lists block mostly ad servers and malware delivery sites.
RLWPX hosts multiple host name block lists. Each list covers a different category of content. There is, for example, an ad blocking list, a porn site blocking list and another list that prevents access to malware hosts. The RLWPX host lists fall between liberal and conservative.
Multiple lists can be used together in one hosts file.
Add each list of blocked hosts into your computer’s hosts file. Do not overwrite the existing hosts file unless you know what you are doing.
What You Will See, Or, Rather, Not See
When a website block list is installed into a computer’s hosts file, access to any of the domains listed in the hosts file will be denied to anyone who uses that computer. The message “Document Not Found” will show in web browsers in place of the content served by the blocked host.
- Ad banners will show as blank, empty squares and rectangles
- Sites known to serve malware will not be able to serve them to your computer
- Web pages will load faster without ads
- Web pages will freeze less frequently.
- Unlike Adblock Plus and other browser based ad blocking methods, websites cannot detect their ads have been blocked so any sites that prevent access based on the presence of ad blocking software will not block you if only hosts file rules are used to block their ads.
The more rules you have in your hosts file, the better your results will be.
If you find you are unable to access certain sites after changing the content of your hosts file, open the hosts file and check that the inaccessible site’s domain name is not listed within it. If it is, remove it and the site will again load as usual. Only you can decide whether the site should or shouldn’t be blocked.
Useful Software
Host Flash (Linux, Android, Unix) downloads hosts files from the sources shown above here, compiles them into one lists of hosts to block then installs them into the hosts file. This software was released by JournalXtra and VR51 to facilitate easy Linux hosts file configuration. The hosts lists used can be chosen when the program runs.
Spybot Search and Destroy (Windows) adds rules to your computer’s hosts file. It doesn’t supply the most comprehensive list but it is an easy option for those who prefer not to manually edit their computer’s system files and the list is regularly updated.
Privoxy (Linux, Windows, Unix, Mac, iOS, FreeBSD) is a web browsing proxy program that helps block ads, scripts and malware as well as anonymizes web access.
Table of Hosts File Locations
| Operating System | Version(s) | Location |
|---|---|---|
| Unix, Unix-like, POSIX | /etc/hosts | |
| Microsoft Windows | 3.1 | %WinDir%\HOSTS |
| 95, 98, ME | %WinDir%\hosts | |
| NT, 2000, XP,[5] 2003, Vista, 2008, 7, 2012, 8, 10 | %SystemRoot%\System32\drivers\etc\hosts | |
| Windows Mobile, Windows Phone | Registry key under HKEY_LOCAL_MACHINE\Comm\Tcpip\Hosts | |
| Apple Macintosh | 9 and earlier | Preferences or System folder |
| Mac OS X 10.0 – 10.1.5[7] | (Added through NetInfo or niload) | |
| Mac OS X 10.2 and newer | /etc/hosts (a symbolic link to /private/etc/hosts) | |
| Novell NetWare | SYS:etc\hosts | |
| OS/2 & eComStation | “bootdrive”:\mptn\etc\ | |
| Symbian | Symbian OS 6.1–9.0 | C:\system\data\hosts |
| Symbian OS 9.1+ | C:\private\10000882\hosts | |
| MorphOS | NetStack | ENVARC:sys/net/hosts |
| AmigaOS | 4 | DEVS:Internet/hosts |
| AROS | ENVARC:AROSTCP/db/hosts | |
| Android | /etc/hosts (a symbolic link to /system/etc/hosts) | |
| iOS | iOS 2.0 and newer | /etc/hosts (a symbolic link to /private/etc/hosts) |
| TOPS-20 | <SYSTEM>HOSTS.TXT | |
| Plan 9 | /lib/ndb/hosts | |
| BeOS | /boot/beos/etc/hosts | |
| Haiku | /boot/common/settings/network/hosts | |
| OpenVMS | UCX | UCX$HOST |
| TCPware | TCPIP$HOST | |
| RISC OS | !Boot.Resources.!Internet.files.Hosts | |
| later boot sequence | !Boot.Choices.Hardware.Disabled.Internet.Files.Hosts |
Note 1: %Windir% and %SystemRoot% represent the storage device that Windows is installed on (usually C:).
Note 2: The data in the table is duplicated from this article at Wikipedia.
Disclaimer
Blocking access to web sites (hosts) will protect a computer and its users from known bad hosts. It won’t prevent access to unknown bad hosts. Ultimately, a computer’s end user is responsible for his or her own protection.
Windows users still need to use antivirus and firewall software when a hosts file block list is used.